Introduction Ethical Hacking
Table of contents
Blogs· 3min March 2, 2023
No system is free of security vulnerabilities, which can be exploited to gain access to restricted resources. Ethical hackers are our allies, using the same techniques as malicious actors to help us find and fix the security vulnerabilities of our systems. In this short introductory article, we explore: the different types of hackers, the goals of ethical hacking and the main activities of ethical hackers.
Types of security vulnerabilities
According to online estimates, the estimated worldwide cost of cybercrime could be as high as $10.5 trillion annually by 2025. Cybercriminals are constantly on the look out for security vulnerabilities and ways to compromise systems through illegal activities such as ransomware, phishing or various types of cyberattacks.
A security vulnerability is a flaw or weakness in a system that can be exploited by malicious actors to gain access to restricted resources. No system is ever fully secure or free of vulnerabilities. Based on their cause, we can identify five types of security vulnerabilities:
- Misconfigurations consist of the incorrect manual configuration of security policies. They are the most commonly occurring vulnerability for cloud resources and APIs.
- Outdated software does not have security patches from software vendors applied to it. The system owners might be slow to apply these updates, exposing themselves to exploitation risk.
- Zero-day vulnerabilities are flaws discovered by malicious actions but have not been fixed by the software vendor yet. Preventing and detecting these kinds of attacks requires a coordinated effort between the organisation and the vendor.
- Compromised user credentials can be used to gain unauthorised access to the system, while appearing as a valid user. Brute force attacks can be used to break weak credentials or they can also be stolen through a previous data breach.
- Network vulnerabilities are caused by exposing either the network's hardware or software through insecure access points or firewalls.
All of the security vulnerabilities presented have a human element to them. The process of securing software involves a constant effort of change control and security review. The table below presents examples of each type of security vulnerability:
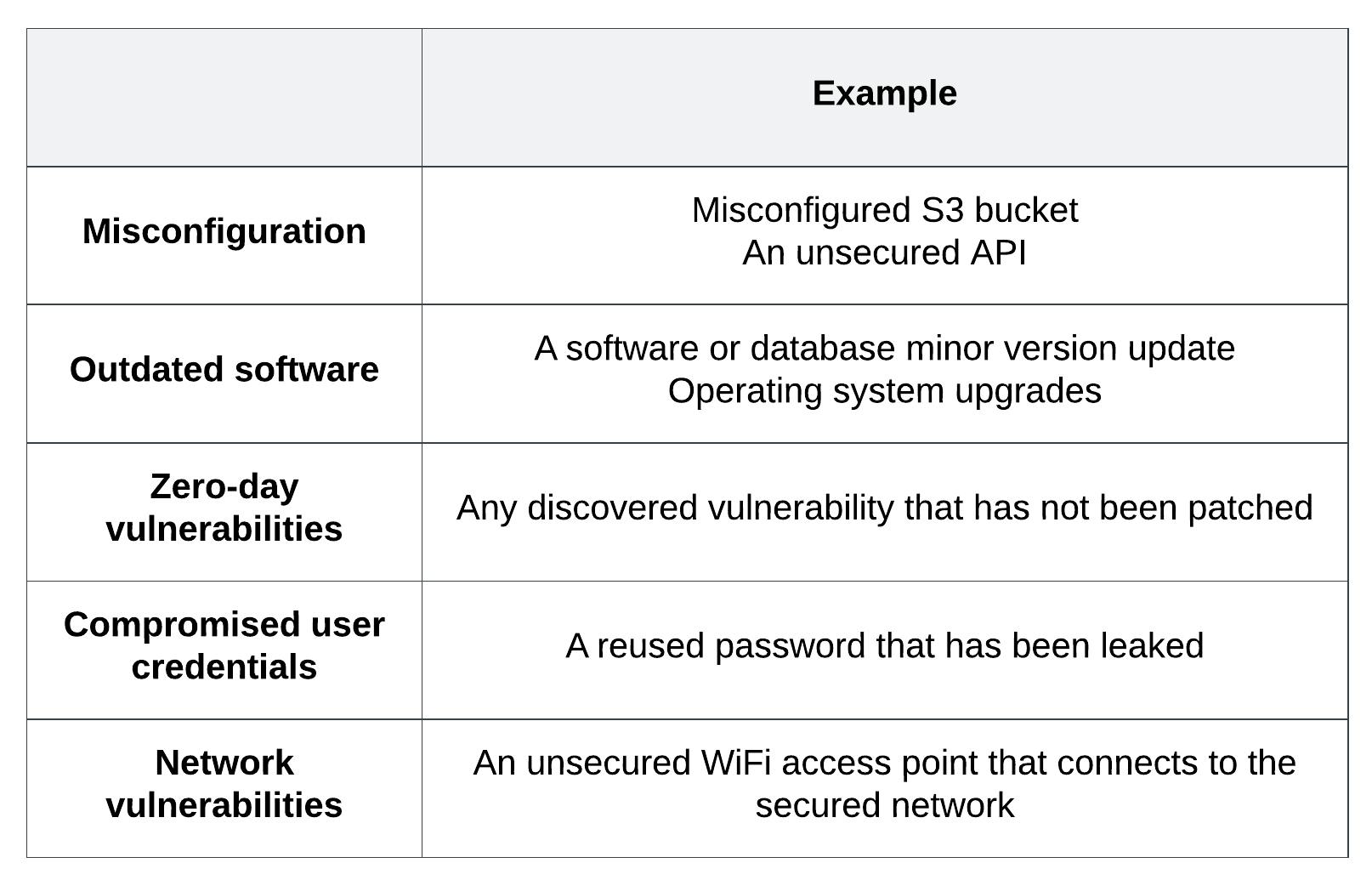
Examples of each vulnerability type
The goal of ethical hacking
Ethical hacking is the practice of testing a system, network or service to find security vulnerabilities. Ethical hackers use the same tools and techniques as malicious hackers, but they undertake this work to support the system owners in securing their system before malicious actors exploit these vulnerabilities.
While they have significant engineering knowledge and skills, ethical hackers operate under a different mindset from engineers. They analyse all possible uses of a resource or library, attempting to uncover errors.
As production systems change and evolve, new vulnerabilities can be introduced by either the system or its third-party dependencies. In effect, this means that no system is fully secured and the work of ethical hackers never stops. They keep up to date with new vulnerabilities discovered in third party tools, assessing their effect on the system they are responsible for and coordinating an action plan to minimise their effect.
Activities of ethical hackers
The tools and techniques required to detect and fix system vulnerabilities vary according to the system under test. They are typically responsible for the following activities:
- Perimeter scanning: also known as external vulnerability scanning, this involves scoping the system's external network to detect if it can be accessible by malicious actors. This involves the analysis of firewalls, gateways and network infrastructure.
- Penetration testing: usually performed before a service or system is live, pentesting is a targeted attack to find exploitable vulnerabilities. The scope of pentesting is very narrow, while the scope of perimeter testing is much wider.
- Red teaming: the ethical hackers launch a full scale cyber attack against the system in order to check how they would respond in the case of a genuine cyber attack. They use all the techniques a real malicious actor would use, including phishing or social engineering of staff.
- Training: ethical hackers are also in charge of educating engineers on good security practices, pushing security best practices into the development process and enable them to take ownership of the security of their services.
Red teaming is the most comprehensive hacking technique, as it tests the system as a whole, including the people using it. The table below presents a comparison of the purpose and focus of each technique:
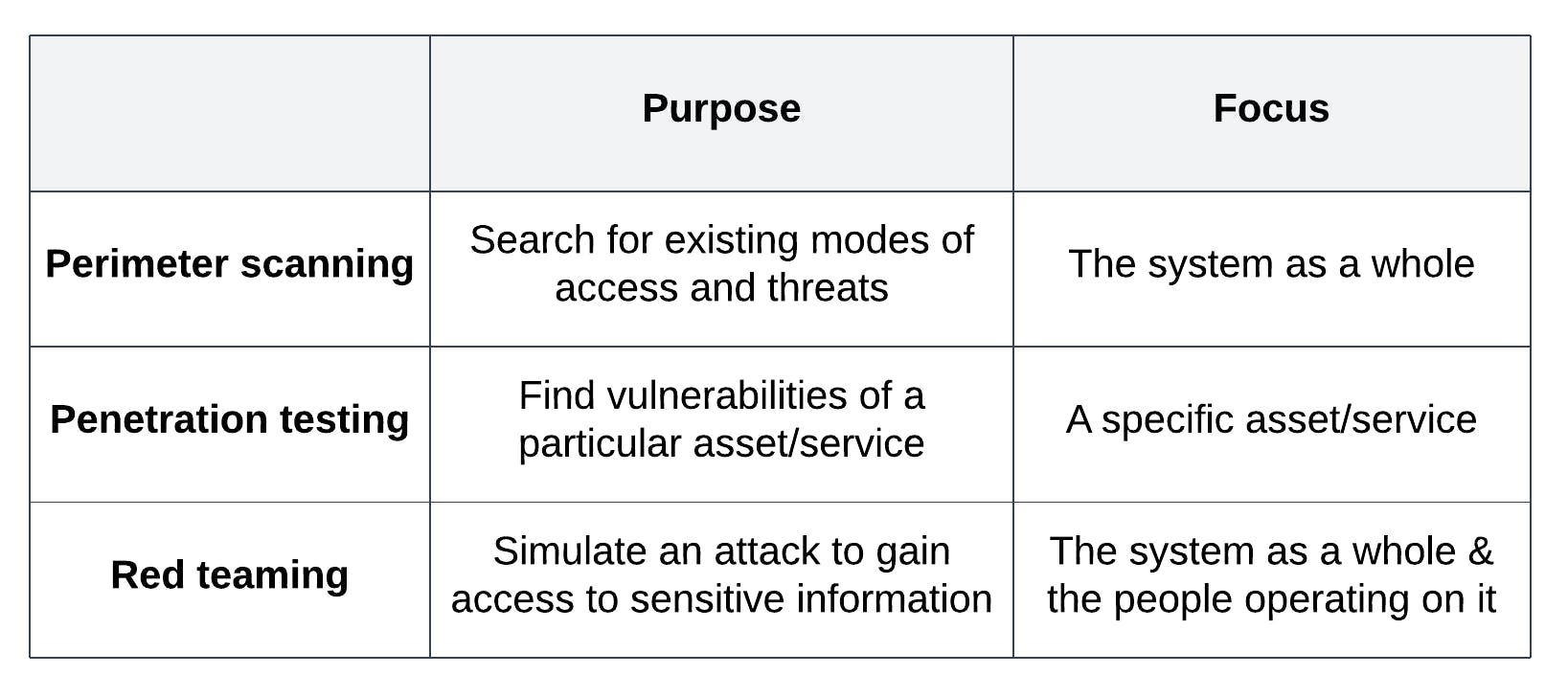
Purpose & focus of each ethical hacking activity
Conclusions
Ethical hacking is an important part of keeping systems secure, as they help us identify and fix vulnerabilities before malicious actors can exploit them.
We have an amazing team of ethical hackers at Form3 to keep our systems, which have access to sensitive financial data, safe.
Further resources
- If you're interested in learning more about hacking, HackTheBox is a great way to upskill.
- You can hear more about ethical hacking on our podcast.
- We have also published interesting articles which demonstrate hacking techniques on our blog: Phishing with GitHub, Adventures into Electron code injection on MacOS, Exploiting Distroless Images, DYLIB Injection in Golang apps on Apple silicon chips
Written by
Adelina is a polyglot engineer and developer relations professional, with a decade of technical experience at multiple startups in London. She started her career as a Java backend engineer, converted later to Go, and then transitioned to a full-time developer relations role. She has published multiple online courses about Go on the LinkedIn Learning platform, helping thousands of developers up-skill with Go. She has a passion for public speaking, having presented on cloud architectures at major European conferences. Adelina holds an MSc. Mathematical Modelling and Computing degree.
Discover more on our blog
Blogs · 10 min
Dangling Danger: Route53's Flawed Dangling NS Record Protection
A subdomain takeover is a class of attack in which an adversary is able to serve unauthorized content from victim's domain name. It can be used for phishing, supply chain compromise, and other forms of attacks which rely on deception. You might've heard about CNAME based or NS based subdomain takeovers.
October 27, 2023
Blogs · 4 min
Applying the Five Ws to Incident Management
In this blogpost, David introduces us to the five W's of information gathering - Who? What? When? Where? Why? Answering the five Ws helps Incident Managers get a deeper understanding of the cause and impact of incidents, not just their remedy, leading to more robust solutions. Fixing the cause of an outage is only just the beginning and the five Ws pave the way for team collaboration during investigations.
July 26, 2023
Blogs · 4 min
.tech Podcast - All about conference speaking
Patrycja, Artur and Marcin are engineers at Form3 and some of our most accomplished speakers. They join us to discuss their motivations for taking up the challenge of becoming conference speakers, tell us how to find events to speak at and share their best advice for preparing engaging talks. They offer advice for new and experienced speakers alike.
July 19, 2023












